💾 Go Back
ELEC 331 - Chapter 1What is InternetProtocolNetwork EdgeEnd SystemsAccess NetworksDigital Subscriber Line (DSL)Cable NetworkHome NetworkEnterprise Access Networks (Ethernet)Wireless Access Networks (WAN)Host TransmissionPhysical MediaGuided MediaUnguided MediaNetwork CoreNetwork Core FunctionsPacket SwitchingStore-and-ForwardQueuing DelayPacket LossCircuit SwitchingFrequency-Division Multiplexing (FDM)Time-Division Multiplexing (TDM)Packet Switching vs. Circuit SwitchingNetwork StructureNetwork of NetworksDelay, Loss, & ThroughputPacket DelayNodal ProcessingQueuing DelayTransmission DelayPropagation DelayPacket LossThroughputProtocol Layer & Service ModelsInternet Protocol StackISO/OSI Reference ModelEncapsulationNetwork SecurityDenial of Service (DoS)Packet SniffingIP SpoofingExercise 1
ELEC 331 - Chapter 1
What is Internet
Hosts / End-Systems: Computing devices that is connected to the Internet. They are called hosts because they host (run) the application-level programs such as a web browser.
Communication Links: Any medium of transfer of information such as fiber, copper, or radio
Bandwidth: Transmission rate of the communication links
Packets: Chunks of data / information
Packet Switches: Device that forwards packets such as routers and switches to their destination.
Route / Path: Sequence of communication links and packet switches traversed by a packet
Protocol
A protocol defines the format and order of messages exchanged between network entities, as well as the actions taken on message transmission / reception. (In other words, a protocol is a communication convention).
An analogy of the network protocol using a human protocol:
Similar thing for a network protocol, we define the format and order of the messages exchanged, as well as the actions taken given a message:
Network Edge
The edge is the ends of the network. Hosts or end systems are part of the edge.
End Systems
End systems or hosts are divided into clients - tablet or PC running a web browser, and servers - data centers.
Access Networks
Access network physically connects an end system to the first router / edge (end system) router. The two of the most prevalent types of broadband residential access is DSL and cable.
Digital Subscriber Line (DSL)
DSL uses existing telephone lines to the central office:
- Data over DSL phone line goes to Internet
- Voice over DSL phone line goes to telephone net
Typically the transmission rate is asymmetrical with < 2.5Mbps upstream and < 25Mbps downstream transmission rate. (Today, the downstream can even go up to 150Mbps using much more advanced signal processing).
Cable Network
Cable internet access requires cable modems, an external device that connects to the home PC through an Ethernet port. Multiple TVs and PCs can connect to the cable network by frequency division multiplexing. However, they will all be sharing a bandwidth.
Frequency Division Multiplexing: Transmitting different channels in different frequency bands.
Cable network has asymmetrical transmission rate of 30Mbps downstream and 2Mbps upstream. The internet access is shared (devices / homes share access network to the cable head-end).
Home Network
Wireless devices such as laptops and phones connect via the wireless access point. Wired connections will connect to the router. Often the wireless access point, router, firewall, and NAT (for allowing multiple devices in the same network) are the same physical device.
Enterprise Access Networks (Ethernet)
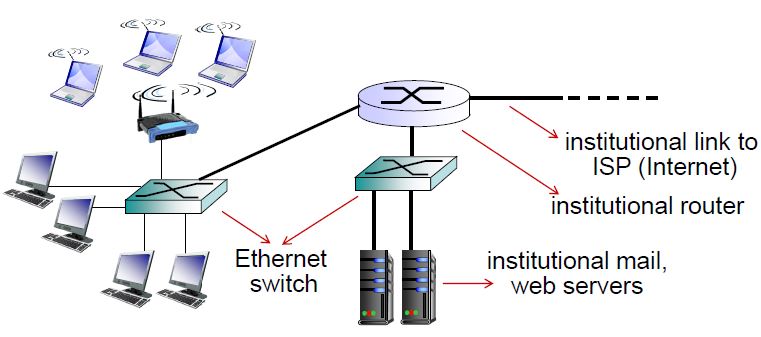
Today, most end systems connect using Ethernet switch. Typically used in companies, universities, and other institutions because of its up to 10Gbps transmission rates.
Wireless Access Networks (WAN)
Shared wireless access network connects end systems to router via base station / access point. There are two types of WAN:
Wireless LANs (local)
- 802.11b/g/n/ac (WiFi)
- Short range (30m)
Wide-area Wireless Access (cellular)
- 3G, 4G (LTE)
- Long range
Host Transmission
The host sending functionality can be described as follows:
- Host takes message from application
- Host breaks it into smaller chunks (packets) of length
- Host transmits packets through the access network at the transmission rate
Physical Media
Bit: Propagates between transmitter/receiver pairs
Physical Link: The connection between transmitter and receiver
Guided Media: Signals propagate in solid media (copper, fibre, etc.)
Unguided Media: Signals propagate freely (radio)
Twisted Pairs (TP): Two insulated copper wires
Guided Media
Coaxial Cable
- Two concentric copper conductors
- Bidirectional
- Broadband - allows multiple channels on the same cable
- Hybrid fiber coax (HFC)
Fiber Optic Cable
- Glass fiber carrying light pulses (each pulse is a bit)
- High speed operation
- Low error rate as repeaters are far apart
- Immune to electromagnetic noise
Unguided Media
Signals carried in electromagnetic spectrum
No physical wire
Bidirectional
Propagation is affected by the environment:
- Reflection
- Obstruction by objects
- Interference
Radio link types:
- Terrestrial microwave (up to 45Mbps channels)
- LAN (WiFi)
- Wide-area (cellular)
- Satellite
Network Core
Network core is a mesh of interconnected packet switches/routers.
Network Core Functions
There are two key functions of a network core. They are Routing and Forwarding.
Routing: Determines source destination route taken by packets using a routing algorithm. The routing algorithm is usually a local forwarding table that looks at the header value of incoming packets and forward it to a corresponding output link

Forwarding: Moves packets from router's input to appropriate router output
Packet Switching
Packet switching is when hosts break application-layer messages into packets and forwards them from one router to next until destination. Each packet is transmitted at full link capacity.
Store-and-Forward
The host sends the packet to the router and the router will wait for the entire packet to arrive before it forwards it. This takes seconds to transmit -bit packet into link at bps.
Example: transmitting Mbits at Mbps
one-top transmission delay seconds (assuming no propagation delay)
Queuing Delay
If the arrival rate of packets to link (from hosts) exceeds transmission rate of link, packets may form a queue when they have to wait to be transmitted on the link.
Packet Loss
If the queue is too long and the memory (buffer) fills up, some packets may be dropped (and information is lost).
Circuit Switching
Circuit switching allows individual users to have dedicated hardware resources. So users get circuit-like performance (good). The service is also fixed and deterministic, so there is not much congestion.
For example when a number is dialed on a wired phone, a physical circuit is created between sending device (phone device) and receiving device.
Frequency-Division Multiplexing (FDM)
In order to link multiple connections, the frequency spectrum of a link is divided up among the connections. (each user gets a frequency).
Time-Division Multiplexing (TDM)
Instead of having different frequencies, the time is divided into time slots. The network dedicates only one slot per frame (time slot) to each connection.
Packet Switching vs. Circuit Switching
Packet switching allows more users to use the network. Since most modern internet applications are "bursty" traffic (low active time) and no point dedicating the whole circuit to everyone all the time, multiplexing using packet switching is more economic.
Example: Consider users sharing a single 1Mbps link. Also assume each user uses 100kbps when active and are only active 10% of the time.
With circuit-switching:
Only 10 users can be supported at all times.
With packet-switching:
More users can be allowed on the same link. For example. 35 users are sharing the same link. The probability of more than 10 users are active at the same time is less than 0.0004. If there are more than 10 people active, there will be queuing delay.
?There is not much that happens if the total users connected is , since the probability of 10 simultaneous active users are still low.
Network Structure
Network of Networks
End systems connect to Internet via Access Internet Service Providers (Access ISP), these ISPs can be residential, company, or university ISPs.
Access ISPs must be interconnected so that hosts can send packets to each other.
Delay, Loss, & Throughput
Loss and delay happens when the packet's arrival rate (from hosts or end systems) exceeds the output link capacity. Thus delay or loss can occur (see queuing delay or packet loss)
Packet Delay
Four Sources of Packet Delay: There are four nodes that contribute to the packet delay:
- Nodal processing
- Queuing delay
- Transmission delay
- Propagation delay
Nodal Processing
Nodal processing (denoted as ) delay is caused by time dedicated to process the incoming information to:
- check packet's header to determine output link
- check bit errors
Typically, this delay is less than a millisecond.
Queuing Delay
Denoted as , queuing delay is time spent waiting for output link for transmission. This depends on how congested the router is (which depends on number of users, and output transmission rate and transmission delay).
Traffic Intensity is used to estimate extend of queueing delay. It is given by:
where is the link bandwidth (bps), is packet length (bits), and is average packet arrival rate.
If the traffic intensity:
- : average queueing delay is small
- : average queueing delay is large
- : average queueing delay is (more packets arriving than packets can be transmitted)
Transmission Delay
Denoted as , see Packet Switching for details.
Propagation Delay
Denoted as is the delay limited by the physics. If is the length of the physical link (distance between the two end systems), and is the propagation speed in the medium (close to speed of light: m/s). Then .
Packet Loss
Since the queue (buffer) has finite capacity, once it becomes full, new packets arriving are dropped (lost).
The lost packet may be retransmitted by previous node, by source end system, or not at all.
Throughput
Throughput: The rate (bits/time unit) at which bits transferred between sender/receiver
- Instantaneous Throughput: Rate at given point in time
- Average: Rate over longer period of time

If , the average end-end throughput would be .
If , the average end-end throughput would be .
Bottleneck Link: The link on end-end path that constrains end-end throughput
Protocol Layer & Service Models
Layer allows dealing with complex systems with explicit structure allows identification and relationship of complex system's pieces. Layering and modularization eases maintenance, and updating of system.
Internet Protocol Stack
Application: Supporting network applications (FTP, SMTP, HTTP)
Transport: Process-to-process data transfer (TCP, UDP)
Network: Routing of datagrams from source to destination (IP, Routing protocols)
Link: Data transfer between neighboring network elements (Ethernet, Wi-Fi)
Physical: Bits on the wire or on radio
ISO/OSI Reference Model
Open Systems Interconnection model contains 7 layers (internet protocol stack + 2 layers). The additional two layers lie below the application layer but above transport layer.
Presentation: Allows application to interpret meaning of data (encryption, compression)
Session: Synchronization, checkpoint, recovery of data exchange
Since the internet protocol stack is missing these two layers, these services (if needed) must be implemented in the application layer.
Encapsulation
As the message is passed to the lower layer at the source, additional information such as header is added.
From application to transport: segment is prepended to the message
From transport to network: datagram is prepended to the segment and message
From network to link: frame is prepended
Network Security
The field involves studying how bad can a network be attacked, how can we defend networks against attacks, and how to design architectures that are immune to attacks.
Host can get malware from virus (self-replicating infection by receiving/executing objects) and worm (self-replicating infection by passively receiving objects that executes itself).
Spyware malware records keystrokes, websites visited.
Infected hosts can be enrolled in botnet and used for spam (DDoS attacks)
Denial of Service (DoS)
Attackers clog the bandwidth / server so that it becomes unavailable to legitimate traffic by overwhelming resource with bogus traffic.
- Select target
- Break into hosts around the network
- Send garbage packets to target from compromised hosts
Packet Sniffing
Packet sniffing works o broadcast media (where Ethernet and wireless networks are shared). They reads/records all packets (including private information).
Wireshark is a free packet-sniffing software.
IP Spoofing
IP spoofing involves faking an address so that packets may be sent using a false source address.
Exercise 1
Q1. What is a protocol?
A protocol is a convention for communication amongst networks. It specifies order, format, and action corresponding to each message communicated.
Q2. List a few access technology (technology needed to connected to internet) used in computer networking
Cable, DSL, Ethernet
Q3. Suppose there is exactly one packet switch between a sending host and a receiving host. The transmission rates between the sending sending host and the switch and between the switch and the receiving host are R1 and R2, respectively. Assuming that the switching uses store-and-forward packet switching, what is the total end-to-end delay to send a packet of length L?
Graphical representation of the connection:
Since the switch uses store-and-forward, the switch needs to receive ALL bits of the packet from the sending host before forwarding to the receiving host.
The delay from the sending host to switch
The delay from the switch to the receiving host
The total delay =
Q4. What advantages does a circuit-switched network have over a packet-switched network?
Since circuit switched network establishes a physical connection between the two edges, the connection will have the advantage of a physical circuit. Also, other's connections won't affect the current connection, so there is no slow downs. The resource is dedicated.
Q5. Why internet is primarily a packet-switched network
Because majority of the traffic / data used on the internet is "bursty" meaning that there is a lot of inactive times. Which will make circuit switching networks very inefficient as a lot of hardware resources are dedicated to connections that are not used.
Also packet-switched network is more scale-able and flexible as it allows more users to connect.
Q6. Suppose users share a 2 Mbps link. Also suppose each user transmits continuously at 1Mbps when transmitting, but each user transmits only 20% of the time.
a. When circuit switching is used, how many users can be supported?
Only 2 users can be supported.
b. For the remainder of this problem, suppose packet switching is used. Why will there be essentially no queuing delay before the link if two or fewer users transmit at the same time? Why will there be a queuing delay if three users transmit at the same time?
For two or less users, the total maximum usage is still under capacity ().
For three or more users the total incoming rate is , but the switch can only support 2 Mbps, thus there will be a queueing delay.
c. Find the probability that a given user is transmitting.
The question is a bit unclear, so I will make a few assumptions and answer them respectively.
Assuming the question is asking the probability of a single user transmitting, then it would be 20% (given by the question)
Assuming the question is asking exactly 1 user is transmitting, then it is
Assuming the question is asking at least 1 user is transmitting, then it is
d. Suppose now there are three users. Find the probability that at any given time, all three users are transmitting simultaneously. Find the faction of time during which the queue grows.
The probability of all three users transmitting is .